#34 waf based sql injection - firewall bypass - ethical hacking @Auouymons

SQL Injection Firewall ( WAF ) BypassПодробнее

WAF bypass using SQL injectionПодробнее

WAF Bypass SQL Injection | Advanced Techniques for Ethical Hacking and CybersecurityПодробнее

Sql Injection in 30 seconds #CyberSecurity #infosec #websecurity #ethicalhacking #dataprotectionПодробнее

#2.7 Bypass Web Application Firewall (WAFs) using Tamper Script via SQLMapПодробнее
Database Breached: The Power of SQL InjectionПодробнее
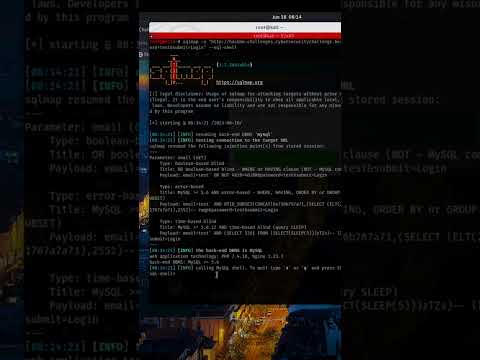
SQLi WAF Bypass Techniques Part 1 - Time-Based AttacksПодробнее

WAF Based SQL Injection | WAF Bypass | Ethical Hacking Course - Educational Purpose VideoПодробнее

Bypass Web Application Firewall (WAF) Manual SQL Injection VulnerabilityПодробнее
Basic Waf Bypass in Sql InjectionПодробнее

What is SQL Injection? | How Hackers Use SQL Injection to Steal DataПодробнее

Bypass with Sql injection with Burpsuit | Advance Burpsuit for Ethical hacking courseПодробнее

SQL Injection Bypass WAFПодробнее

SQL Injection | Hack the Box | FacultyПодробнее
Hard Waf Bypass SQL InjectionПодробнее

SQL Injection Using WAF Bypass | Manual SQL Injection | SQL Injection for Beginners| Ethical HackingПодробнее

Find SQL Injection vulnerability with sqlmapПодробнее
34. Bypassing Logins Using SQL Injection VulnerabilityПодробнее
